Browser Overview and Components
Browsers like Chrome and Safari are have an estimated user base of more than 3 billion monthly active users with Chrome being at ~60% of the user-base and Safari having ~17%.

Chrome uses the Blink Rendering Engine and V8 JS Engine while Safari relies on the Webkit Webcore Rendering Engine and JavaScriptCore JS Engine. These browser's complexity rivals the OS they run on with Chromium standing at 44 millions LOC and Webkit having around 32 millon.
So the question is: here do you even start to find bugs in software this big? To do it you need to brake it down into smaller parts.
Browser Stack
Browsers are built up on layered components
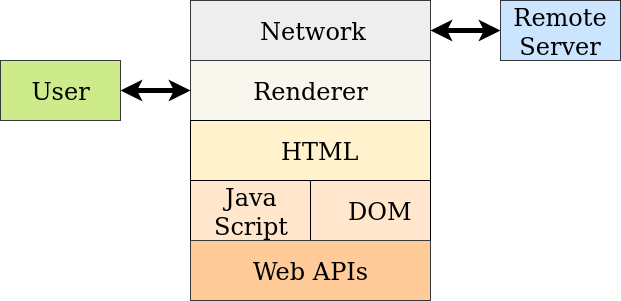

Browsers Processes
Browsers are separated into many processes with security boundaries; we can see them in programs like Task Manager or ps. If we do so we'll see that most processes have a --type=renderer flag which makes them a renderer process: these processes are in charge of processing, executing and displaying the requested web pages (which is why they are sometimes called Content Processes).
This makes the renderer processes the first target of a full-chain browser exploit and that's why they are sandboxes to help protect users from RCE.
In Chrome we can see a breakdown of the different kinds of processes
Main Browser processes
Tab processes
Extension processes
GPU processes
It's possible or tabs to share the same process.
The following is the general architecture browser processes follow

Web Standards & Specifications
W3C - HTML related standards, CSS
ECMA - JavaScript standards
...
WebIDL (or Web Interface Definition Language) is another specification browser components need to interface with other components and we can see an example of how it works here
What WebIDL does is defining an API over browser components and convert them into C++ code before compiling, this makes it so components can include header files to interface and both Chrome and Safari can use WebIDL.
Safari
The Safari Browser wraps WebKit with some added OS X specifics.
Webkit originated from KHTML in 2001 within Apple
Open-sourced around 2005
Managed though SVN
Primary components are WebCore and JavaScriptCore
WebCore is the rendering engine
JavaScriptCore is the JavaScript engine
Chrome
Chrome uses the Chromium browser engine, released open-source in 2008 by Google.
Rendering engine called Blink
Originally used WebCore, forked to blink in 2013
JavaScript engine called V8
Originated with the first chrome version in 2008
Last updated