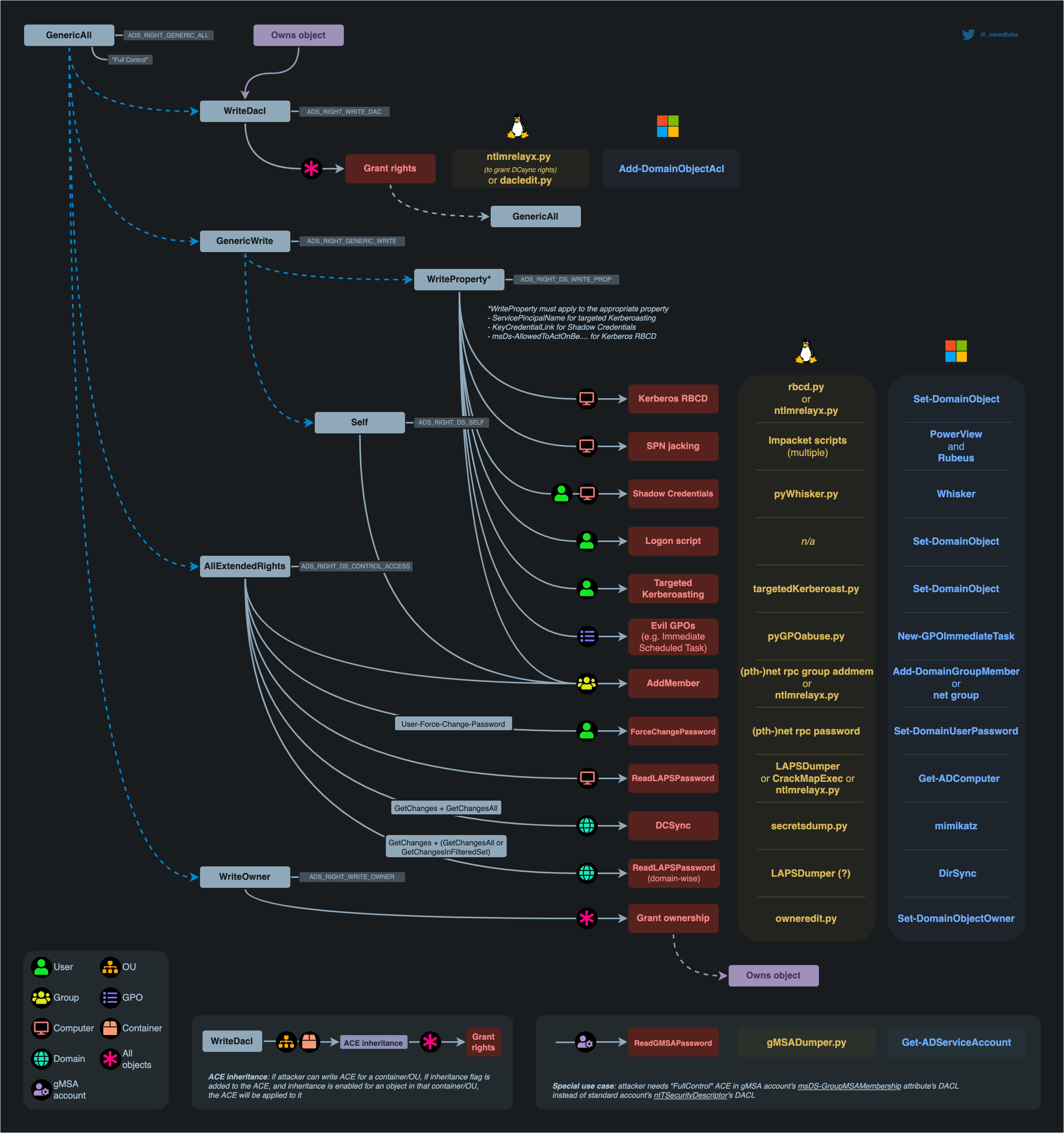
DACLs Enumeration
DSACLS
dsacls.exe "cn=otter,cn=users,dc=domain,dc=com"dsacls.exe "cn=otter,cn=users,dc=domain,dc=com" | Select-String "anotherUser" -Context 5,5Powershell
$directorySearcher = New-Object System.DirectoryServices.DirectorySearcher('(samaccountname=otter)')
$directorySearcher.SecurityMasks = [System.DirectoryServices.SecurityMasks]::Dacl -bor [System.DirectoryServices.SecurityMasks]::Owner
$binarySecurityDescriptor = $directorySearcher.FindOne().Properties.ntsecuritydescriptor[0]
$parsedSecurityDescriptor = New-Object System.DirectoryServices.ActiveDirectorySecurity
$parsedSecurityDescriptor.SetSecurityDescriptorBinaryForm($binarySecurityDescriptor)
$parsedSecurityDescriptor.Access$parsedSecurityDescriptor.Access | Where-Object {$_.IdentityReference -like '*anotherUser*'}Impacket's dacledit
dacleditBloodHound
Last updated